National defense means something very different in 2021 than it did even a generation ago, as new types of threats emerge constantly. No country can afford to be stuck fighting the last war—something the French learned all too well as a result of the Nazi blitzkrieg. Right now, cyberattacks are the newest innovation in warfare.
While they may not enable an army to roll across our borders, defeat our military, and conquer us in the traditional sense, cyberattacks have caused real damage that has affected the lives of our fellow Americans. The next ones could do far worse. Thankfully, and unlike the twice impeached former guy, President Biden is making cyberattacks one of his administration’s highest defense priorities.
On the one hand, the threat caused by someone hacking into computer systems, including those of our government, has been around for decades. Matthew Broderick’s character in WarGames accidentally almost destroyed the world by starting a nuclear war before the computer famously learned that when it comes to such a conflict, “the only winning move is not to play.” Apparently, that movie had a tangible influence on policy, leading to actual legislation. In the real world of today, cyberattacks are the farthest thing from unintentional.
Below is a brief summary of their impact from the Heritage Foundation (I may not agree with their typically Republican recommendations on how to respond, which rely too heavily on private industry, but this is straightforward information):
The Center for Strategic and International Studies listed 56 “significant cyber incidents” from around the world just in the first five months of 2021. You can check out the full list going back to the start of 2006 here.
Leon Panetta, former secretary of defense under President Obama, ominously warned in 2012 that “a cyber attack perpetrated by nation-states or violent extremist groups could be as destructive as the terrorist attack on 9/11.” Panetta added, “Such a destructive cyber-terrorist attack could virtually paralyze the nation.” He laid out some specific scenarios of just how this might play out:
YouTube Video
In an interview with the Wall Street Journal earlier this month, current FBI Director Christopher Wray also noted “parallels” between the threat posed by contemporary cyberattacks and what happened on 9/11.
We’ve all been hearing about cyberattacks against the U.S. government, American institutions, and infrastructure. There was the SolarWinds attack in December 2020, which The Guardian described as “the worst-ever” our government has suffered. NPR dug deep and four months later published a report detailing how the Russians pulled the whole thing off. In summary, the Russian government, specifically its foreign intelligence service known as SVR, hacked into around 100 U.S. companies (Microsoft, Intel, and Cisco were among them), and a dozen federal departments, such as Defense, Treasury, Justice, and Energy. There’s one other worth mentioning; the Russians also broke into the Cybersecurity and Infrastructure Security Agency (CISA) which, of course, is tasked with preventing exactly such breaches of federal systems. Unlike most of the events in a certain song by Alanis Morissette, that’s actually highly ironic. Please note that Trump had fired CISA’s director, Christopher Krebs, a month earlier—not because of any concerns Trump had about cybersecurity, but because Krebs had rejected his boss’s Big Lie about the 2020 election being fraudulent. We don’t know whether Krebs’ removal made it easier for the hackers to breach our systems, but either way the firing demonstrates how little value The Orange Menace assigned to this issue.
Although I mostly want to look at how President Biden is responding to these kinds of attacks, it’s important to properly assess the failure of his predecessor, aka Putin’s puppet, on cyberattacks. Lest we forget, there was a pantsuit-wearing popular vote winner who, on a debate stage in 2016, all but predicted these failures if her opponent became president:
Unfortunately for us, Trump appeared more interested in sending U.S. military forces into space than confronting cybersecurity threats. The Orange Julius Caesar didn’t want to elevate cybersecurity because he feared it might somehow draw more attention to the Russian hack of the Democratic National Committee in 2016, and his campaign’s interactions with Russian officials more broadly, thus further delegitimizing his Electoral College victory. So he essentially ignored the threat. As the New York Times pointed out in March 2020, Trump’s own staff “is famously reluctant to bring cybersecurity issues to his desk” for exactly that reason.
This despite the fact that his own Homeland Security Secretary Kirstjen Nielsen, declared in 2018 that we faced a “pandemic” (oh boy) of cyberattacks, and added “cyberspace is now the most active battlefield, and the attack surface extends into every single American home.” She said this only four months after the Trump administration had axed the position of White House cybersecurity coordinator, an official who sat on the National Security Council. The irony just flows.
Overall the Trump record was so bad on this issue that Politico called him the “anti-cyber security president.” As CNN’s Brianna Keilar put it: “Very few elected U.S. officials get a medal for cybersecurity achievements but former President Trump doesn't even get a participation award.” The Electronic Frontier Foundation’s executive director, Cindy Cohn, offered that even the positive things that happened under his watch “seemed to occur despite the repeated attempted politicization of the work, not because of any Trump administration leadership or initiatives.”
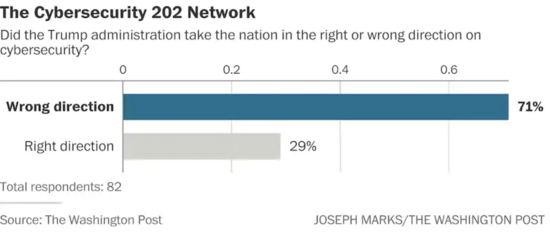
This Washington Post piece offers a comprehensive analysis of the four years of cybersecurity incompetence that flowed from the top. According to a panel of 82 experts, the overwhelming majority contended that Trump made things worse on this issue. Did I mention that the survey was conducted before the SolarWinds hack?
The idiot-in-chief maintained his willfully ignorant approach right to the end. When his own intelligence services determined that Russia was behind the SolarWinds debacle—even his Sec. of State Mike Pompeo had said so—he blamed the media and spouted “it may” be China. Actually he said “it may!”—punctuation is very important to Trump.
After SolarWinds, then president-elect Biden promised that those found culpable of committing cyberattacks would pay “substantial costs” once he became president, adding: “I will not stand idly by in the face of cyberassaults on our nation.” He continued: “a good defense isn’t enough; we need to disrupt and deter our adversaries from undertaking significant cyberattacks in the first place.”
So let’s look at how the Biden White House has responded thus far—with the caveat that some of the things they are doing likely remain secret, and we won’t be able to comprehensively judge his record on cyber for some time.
On April 12, Biden nominated Chris Inglis, who worked for 28 years at the National Security Agency (NSA), including seven years as its deputy director, to be the country’s first ever national cyber director. Given the old saying that personnel is policy, this is a very promising step. The New York Times praised the choice: “Mr. Inglis has embraced what the Pentagon calls a “defend forward” strategy, in which the U.S. goes into foreign networks, hunting for gathering threats. In recent years, he has been unsparing in his criticism of how disorganized American defenses remain more than a decade into the era of daily cyberconflict.” Inglis is part of a troika of highly regarded experts who will head up the U.S. cyber defense team.
Three days later, the White House announced a new round of sanctions against Russia, in part over SolarWinds, but also over their having meddled in our presidential election for the second consecutive time, as well as their continued occupation of Crimea. The sanctions include measures aimed at punishing Russia specifically on cyber:
Plus, the administration took proactive steps to combat cyberattacks going forward. It will “provid[e] a first-of-its kind course for policymakers worldwide on the policy and technical aspects of publicly attributing cyber incidents” as well as “training to foreign ministry lawyers and policymakers on the applicability of international law to state behavior in cyberspace.”
There have been other ransomware attacks in recent weeks since the April sanctions were issued, including ones on the Colonial gas pipeline, and on JBS, a meat packing company, that had a disruptive if temporary impact on our economy. The Colonial breach led to “higher pump prices, panic buying, and gas stations running out of fuel” that lasted for the better part of a week up and down the East Coast. The JBS attack forced meat processing plants to halt operations in the U.S. and Australia for more than a day, which could have resulted in a huge spike in prices and a disruption in the food supply. Imagine what would have happened if we had been unable to reverse the effects of the breaches as quickly as we did. Both attacks, which occurred in May, appear to have emanated from Russian territory, and the Biden administration has made clear it holds Russia responsible.
Only a handful of days after the Colonial pipeline attack, the White House issued a wide-ranging executive order on cybersecurity. It led with the vitally important point that, while the government is responsible for defending its own computer systems, much of our infrastructure is in private hands, so companies must also step up and do their part to prevent cyberattacks: “Cybersecurity requires more than government action. Protecting our Nation from malicious cyber actors requires the Federal Government to partner with the private sector. The private sector must adapt to the continuously changing threat environment, ensure its products are built and operate securely, and partner with the Federal Government to foster a more secure cyberspace.”
The EO went on to list actions on a wide array of topics, each of which received its own section:
Normally, this is the part where I urge you to read the entire document if you want more details. And don’t get me wrong, this stuff is important. But if you aren’t a cybersecurity expert yourself, then rather than urge you, I’ll challenge you to read it all without nodding off. Seriously, though, the document reflects a president who, finally, is giving this issue the attention it deserves.
Then, after the JBS hacking, Biden and his team ratcheted up their response even further. White House spokesperson Karine Jean-Pierre stated: "The White House is engaging directly with the Russian government on this matter and delivering the message that responsible states do not harbor ransomware criminals." Press secretary Jen Psaki added: “We're not taking any options off the table in terms of how we may respond." She also announced that Biden "has launched a rapid strategic review to address the increased threat of ransomware to include four major lines of effort"—these include hitting the infrastructure that supports those who engage in ransomware attacks. The president himself refused to rule out retaliating against Moscow: “We’re looking closely at that issue.”
NBC News spoke to sources inside and outside the government, and reported earlier this month: “The Biden administration is moving to treat ransomware attacks as a national security threat, using intelligence agencies to spy on foreign criminals and contemplating offensive cyber operations against hackers inside Russia.” According to one ex-government official, “Right now, [the administration’s] hair [is] on fire.” It’s worth noting that another recent Russian hacking attempt—this one aimed at the U.S. Agency for International Development—was discovered and blocked relatively quickly, which, according to White House officials, demonstrates that the newly instituted defense measures were bearing fruit.
Last Wednesday’s summit offered Biden an opportunity to directly confront Putin over these cyberattacks. Beforehand, Secretary of State Antony Blinken explained in an interview with Axios’ Mike Allen that the meeting was going to happen “not in spite of” these incidents, but rather “because of them.” Blinken further noted that the American president will basically warn his Russian counterpart to knock off this kind of behavior, by telling him “directly and clearly what he can expect from the United States if aggressive, reckless actions toward us continue.” National security adviser Jake Sullivan also commented: “Ransomware attacks against critical infrastructure are of an even higher order of magnitude of concern for us, whether that's about a pipeline, or a meat supply, or a hospital system, or other areas of critical infrastructure. The president will talk to President Putin about our concerns on this front.”
In the run-up to the summit, Putin expressed openness to some kind of mutual exchange of cyber-criminals with the U.S. Biden said this was “potentially a good sign” but, in a follow-up, Sullivan pointed out that if people in the U.S. break the law, our system already holds them accountable, as opposed to how Moscow handles their citizens’ illicit activities. If Putin wants to start doing the same, then that’s great, but, Sullivan added: "This is not about exchanges or swaps, or anything like that."
Just after the summit concluded, the Washington Post noted that the expectations for “making any progress” at all on cyber were “set exceedingly low.” In their assessment, Biden cleared the bar. Other commentators agreed, with the USA Today Editorial Board noting “America reclaimed some lost pride Wednesday when President Joe Biden met in Geneva with Russian President Vladimir Putin—and did so without bowing and scraping to a smug and devious autocrat.” As for the assessment of Trump and his party apparatchiks, it was as hypocritical as anything they’ve said since 2016, and that really is saying something. The president himself expressed optimism going forward, and pushed back at those critics who might confuse his approach for naivete or a lack of guile. Always publicly focusing on the negatives, he argued, would simply “guarantee nothing happens.”
On the cyber-related specifics, first of all, Biden delivered to Putin the warning he’d promised:
Second, the two leaders came to an understanding on boundaries. Biden laid out the terms: “We agreed to task experts in both our countries to work on specific understandings about what's off-limits [for hacking] and to follow up on specific cases that originate in … either of our countries.” Putin, for his part, denied his government was behind any of the recent cyberattacks. While Trump may have accepted such a denial as truthful, Biden is, fortunately for us, not Trump.
Here’s the takeaway in the words of James Lewis, who served in a high-level government position on cyber, “Biden delivered the right message. If the Russians didn’t know we were serious, it’s unavoidable now. But Putin isn’t going to make any concessions. They’re going to test us. …The next phase is coming up with ways to more comprehensively threaten them or to actually use our cyber capabilities.”
Regarding that next phase, on the heels of a NATO summit the weekend before last, the 30-nation alliance collectively declared: “the impact of significant malicious cumulative cyber activities might, in certain circumstances, be considered as amounting to an armed attack.” If such a determination was made, it could result in Article 5 being invoked. If that happened, all NATO member states would be required to come to the aid of the country facing attacks.
The NATO statement specifically cited Russia for having engaged in “malicious cyber activities; and turning a blind eye to cyber criminals operating from its territory, including those who target and disrupt critical infrastructure in NATO countries,” and continued: “we will make greater use of NATO as a platform for political consultation among Allies, sharing concerns about malicious cyber activities, and exchanging national approaches and responses, as well as considering possible collective responses. If necessary, we will impose costs on those who harm us.” This represents Joe Biden sending a message that cyberattacks on the U.S. will bring a response not just from us, but from our allies as well.
In summary, there’s a strong consensus that the 46th president is acting far more assertively as well as effectively on cyberattacks than did the 45th—especially in regards to Russia. Trump’s homeland security adviser Tom Bossert complimented Biden for having “indicated his willingness to hold Russia accountable in some way for the pipeline attack, even though it was carried out by a criminal organization,” and noted: “that's a big leap forward.” April Falcon Doss, who worked for more than ten years at the NSA, also praised the new administration’s approach.
In a success achieved in just the last two weeks, the Biden Department of Justice snatched back a majority of the loot ransomed by the Russian hackers who hit Colonial. I’d love to have been a fly on the wall (in the borscht?) when Vlad heard that news. People in the know when it comes to cybersecurity offered kudos on this action. Here’s what John Hultquist, an executive at FireEye, a cybersecurity company, had to say: “It has become clear that we need to use several tools to stem the tide [of ransomware attacks]…. A stronger focus on disruption may disincentivize this behavior, which is growing in a vicious cycle.” In other words, sometimes the best defense is a good offense.
Although China has also been responsible for a number of cyberattacks on the United States, including since Biden took office, it is clear that Russia is the primary bad actor on this front. One thing we know is that the current president will never be Vladimir Putin’s puppet—Trump, on the other hand, continues to be exactly that.
Republicans have long loved to trumpet their supposed credentials on national security. However, Democrats are in fact the ones who’ve better protected Americans from our adversaries abroad. Before 9/11, George W. Bush ignored Bill Clinton’s warning that Osama bin Laden would be our country’s greatest national security threat, and then went on to ignore multiple, specific warnings about an “imminent” attack that would result in “dramatic consequences”—and we’re not just talking about the famous “Bin Laden Determined to Strike in U.S.” presidential daily brief he received five weeks beforehand. That blunder, compounded by the decision to invade not only Afghanistan but Iraq, made Dubya the worst foreign policy and national security president in our history. Barack Obama, on the other hand, took out bin Laden and succeeded in leaving our country in a far better position than he found it on those fronts (as well as many others).
The Man Who Lost An Election And Tried To Steal It may not have done something as devastatingly harmful to our interests—not to mention the horrors unleashed on those living (and dying) in the region. Nevertheless, on cyberdefense, his lack of attention and lack of action were unconscionable. Trump’s malpractice left us highly vulnerable to the attacks we’ve faced in recent months, both before and after he grudgingly left office. President Biden will be judged on how well he is able to clean up the mess he inherited. He has already taken substantive steps toward achieving that objective.
Biden understands that the first and most important job of any president of the United States is to protect America, and today that includes protecting our computer systems and cyberinfrastructure. My gut tells me that he won’t let us down.
Ian Reifowitz is the author of The Tribalization of Politics: How Rush Limbaugh's Race-Baiting Rhetoric on the Obama Presidency Paved the Way for Trump (Foreword by Markos Moulitsas)
While they may not enable an army to roll across our borders, defeat our military, and conquer us in the traditional sense, cyberattacks have caused real damage that has affected the lives of our fellow Americans. The next ones could do far worse. Thankfully, and unlike the twice impeached former guy, President Biden is making cyberattacks one of his administration’s highest defense priorities.
On the one hand, the threat caused by someone hacking into computer systems, including those of our government, has been around for decades. Matthew Broderick’s character in WarGames accidentally almost destroyed the world by starting a nuclear war before the computer famously learned that when it comes to such a conflict, “the only winning move is not to play.” Apparently, that movie had a tangible influence on policy, leading to actual legislation. In the real world of today, cyberattacks are the farthest thing from unintentional.
Below is a brief summary of their impact from the Heritage Foundation (I may not agree with their typically Republican recommendations on how to respond, which rely too heavily on private industry, but this is straightforward information):
FACT: Cyberattacks and espionage are costly to the U.S. and global economy.
Cyber breaches are projected to cost the global economy $2.1 trillion by 2019, more than quadrupling the cost since 2015.
IBM’s 2016 Cyber Security Intelligence Index says that health care, financial services, and manufacturing are the top three sectors targeted by hackers due to the vast quantity of personal information and potential monetary gain that exist in those fields.
The Center for Strategic and International Studies listed 56 “significant cyber incidents” from around the world just in the first five months of 2021. You can check out the full list going back to the start of 2006 here.
Leon Panetta, former secretary of defense under President Obama, ominously warned in 2012 that “a cyber attack perpetrated by nation-states or violent extremist groups could be as destructive as the terrorist attack on 9/11.” Panetta added, “Such a destructive cyber-terrorist attack could virtually paralyze the nation.” He laid out some specific scenarios of just how this might play out:
“An aggressor nation or extremist group could use these kinds of cyber tools to gain control of critical switches. They could for example derail passenger trains, or even more dangerous trains loaded with lethal chemicals. They could contaminate the water supply in major cities, or shut down the power grid across large parts of the country. The most destructive scenarios involve cyber actors launching several attacks on our critical infrastructure at one time in combination with a physical attack on our country. Attackers could also seek to disable or degrade critical military systems and communication networks.”
YouTube Video
In an interview with the Wall Street Journal earlier this month, current FBI Director Christopher Wray also noted “parallels” between the threat posed by contemporary cyberattacks and what happened on 9/11.
We’ve all been hearing about cyberattacks against the U.S. government, American institutions, and infrastructure. There was the SolarWinds attack in December 2020, which The Guardian described as “the worst-ever” our government has suffered. NPR dug deep and four months later published a report detailing how the Russians pulled the whole thing off. In summary, the Russian government, specifically its foreign intelligence service known as SVR, hacked into around 100 U.S. companies (Microsoft, Intel, and Cisco were among them), and a dozen federal departments, such as Defense, Treasury, Justice, and Energy. There’s one other worth mentioning; the Russians also broke into the Cybersecurity and Infrastructure Security Agency (CISA) which, of course, is tasked with preventing exactly such breaches of federal systems. Unlike most of the events in a certain song by Alanis Morissette, that’s actually highly ironic. Please note that Trump had fired CISA’s director, Christopher Krebs, a month earlier—not because of any concerns Trump had about cybersecurity, but because Krebs had rejected his boss’s Big Lie about the 2020 election being fraudulent. We don’t know whether Krebs’ removal made it easier for the hackers to breach our systems, but either way the firing demonstrates how little value The Orange Menace assigned to this issue.
Honored to serve. We did it right. Defend Today, Secure Tomrorow. #Protect2020
— Chris Krebs (@C_C_Krebs) November 18, 2020
Although I mostly want to look at how President Biden is responding to these kinds of attacks, it’s important to properly assess the failure of his predecessor, aka Putin’s puppet, on cyberattacks. Lest we forget, there was a pantsuit-wearing popular vote winner who, on a debate stage in 2016, all but predicted these failures if her opponent became president:
“You won’t admit that the Russians have engaged in cyber attacks against the United States of America.” —Sec. of State Hillary Clinton to then-candidate Donald Trump
Unfortunately for us, Trump appeared more interested in sending U.S. military forces into space than confronting cybersecurity threats. The Orange Julius Caesar didn’t want to elevate cybersecurity because he feared it might somehow draw more attention to the Russian hack of the Democratic National Committee in 2016, and his campaign’s interactions with Russian officials more broadly, thus further delegitimizing his Electoral College victory. So he essentially ignored the threat. As the New York Times pointed out in March 2020, Trump’s own staff “is famously reluctant to bring cybersecurity issues to his desk” for exactly that reason.
This despite the fact that his own Homeland Security Secretary Kirstjen Nielsen, declared in 2018 that we faced a “pandemic” (oh boy) of cyberattacks, and added “cyberspace is now the most active battlefield, and the attack surface extends into every single American home.” She said this only four months after the Trump administration had axed the position of White House cybersecurity coordinator, an official who sat on the National Security Council. The irony just flows.
Overall the Trump record was so bad on this issue that Politico called him the “anti-cyber security president.” As CNN’s Brianna Keilar put it: “Very few elected U.S. officials get a medal for cybersecurity achievements but former President Trump doesn't even get a participation award.” The Electronic Frontier Foundation’s executive director, Cindy Cohn, offered that even the positive things that happened under his watch “seemed to occur despite the repeated attempted politicization of the work, not because of any Trump administration leadership or initiatives.”
This Washington Post piece offers a comprehensive analysis of the four years of cybersecurity incompetence that flowed from the top. According to a panel of 82 experts, the overwhelming majority contended that Trump made things worse on this issue. Did I mention that the survey was conducted before the SolarWinds hack?

The idiot-in-chief maintained his willfully ignorant approach right to the end. When his own intelligence services determined that Russia was behind the SolarWinds debacle—even his Sec. of State Mike Pompeo had said so—he blamed the media and spouted “it may” be China. Actually he said “it may!”—punctuation is very important to Trump.
After SolarWinds, then president-elect Biden promised that those found culpable of committing cyberattacks would pay “substantial costs” once he became president, adding: “I will not stand idly by in the face of cyberassaults on our nation.” He continued: “a good defense isn’t enough; we need to disrupt and deter our adversaries from undertaking significant cyberattacks in the first place.”
So let’s look at how the Biden White House has responded thus far—with the caveat that some of the things they are doing likely remain secret, and we won’t be able to comprehensively judge his record on cyber for some time.
On April 12, Biden nominated Chris Inglis, who worked for 28 years at the National Security Agency (NSA), including seven years as its deputy director, to be the country’s first ever national cyber director. Given the old saying that personnel is policy, this is a very promising step. The New York Times praised the choice: “Mr. Inglis has embraced what the Pentagon calls a “defend forward” strategy, in which the U.S. goes into foreign networks, hunting for gathering threats. In recent years, he has been unsparing in his criticism of how disorganized American defenses remain more than a decade into the era of daily cyberconflict.” Inglis is part of a troika of highly regarded experts who will head up the U.S. cyber defense team.
Three days later, the White House announced a new round of sanctions against Russia, in part over SolarWinds, but also over their having meddled in our presidential election for the second consecutive time, as well as their continued occupation of Crimea. The sanctions include measures aimed at punishing Russia specifically on cyber:
Treasury designated six Russian technology companies that provide support to the Russian Intelligence Services’ cyber program, ranging from providing expertise to developing tools and infrastructure to facilitating malicious cyber activities. These companies are being designated for operating in the technology sector of the Russian Federation economy. We will continue to hold Russia accountable for its malicious cyber activities, such as the SolarWinds incident, by using all available policy and authorities.
Plus, the administration took proactive steps to combat cyberattacks going forward. It will “provid[e] a first-of-its kind course for policymakers worldwide on the policy and technical aspects of publicly attributing cyber incidents” as well as “training to foreign ministry lawyers and policymakers on the applicability of international law to state behavior in cyberspace.”
There have been other ransomware attacks in recent weeks since the April sanctions were issued, including ones on the Colonial gas pipeline, and on JBS, a meat packing company, that had a disruptive if temporary impact on our economy. The Colonial breach led to “higher pump prices, panic buying, and gas stations running out of fuel” that lasted for the better part of a week up and down the East Coast. The JBS attack forced meat processing plants to halt operations in the U.S. and Australia for more than a day, which could have resulted in a huge spike in prices and a disruption in the food supply. Imagine what would have happened if we had been unable to reverse the effects of the breaches as quickly as we did. Both attacks, which occurred in May, appear to have emanated from Russian territory, and the Biden administration has made clear it holds Russia responsible.
Only a handful of days after the Colonial pipeline attack, the White House issued a wide-ranging executive order on cybersecurity. It led with the vitally important point that, while the government is responsible for defending its own computer systems, much of our infrastructure is in private hands, so companies must also step up and do their part to prevent cyberattacks: “Cybersecurity requires more than government action. Protecting our Nation from malicious cyber actors requires the Federal Government to partner with the private sector. The private sector must adapt to the continuously changing threat environment, ensure its products are built and operate securely, and partner with the Federal Government to foster a more secure cyberspace.”
The EO went on to list actions on a wide array of topics, each of which received its own section:
Removing Barriers to Sharing Threat Information
Modernizing Federal Government Cybersecurity
Enhancing Software Supply Chain Security
Establishing a Cyber Safety Review Board
Standardizing the Federal Government’s Playbook for Responding to Cybersecurity Vulnerabilities and Incidents
Improving Detection of Cybersecurity Vulnerabilities and Incidents on Federal Government Networks
Improving the Federal Government’s Investigative and Remediation Capabilities
National Security Systems
Normally, this is the part where I urge you to read the entire document if you want more details. And don’t get me wrong, this stuff is important. But if you aren’t a cybersecurity expert yourself, then rather than urge you, I’ll challenge you to read it all without nodding off. Seriously, though, the document reflects a president who, finally, is giving this issue the attention it deserves.
Then, after the JBS hacking, Biden and his team ratcheted up their response even further. White House spokesperson Karine Jean-Pierre stated: "The White House is engaging directly with the Russian government on this matter and delivering the message that responsible states do not harbor ransomware criminals." Press secretary Jen Psaki added: “We're not taking any options off the table in terms of how we may respond." She also announced that Biden "has launched a rapid strategic review to address the increased threat of ransomware to include four major lines of effort"—these include hitting the infrastructure that supports those who engage in ransomware attacks. The president himself refused to rule out retaliating against Moscow: “We’re looking closely at that issue.”
NBC News spoke to sources inside and outside the government, and reported earlier this month: “The Biden administration is moving to treat ransomware attacks as a national security threat, using intelligence agencies to spy on foreign criminals and contemplating offensive cyber operations against hackers inside Russia.” According to one ex-government official, “Right now, [the administration’s] hair [is] on fire.” It’s worth noting that another recent Russian hacking attempt—this one aimed at the U.S. Agency for International Development—was discovered and blocked relatively quickly, which, according to White House officials, demonstrates that the newly instituted defense measures were bearing fruit.
Last Wednesday’s summit offered Biden an opportunity to directly confront Putin over these cyberattacks. Beforehand, Secretary of State Antony Blinken explained in an interview with Axios’ Mike Allen that the meeting was going to happen “not in spite of” these incidents, but rather “because of them.” Blinken further noted that the American president will basically warn his Russian counterpart to knock off this kind of behavior, by telling him “directly and clearly what he can expect from the United States if aggressive, reckless actions toward us continue.” National security adviser Jake Sullivan also commented: “Ransomware attacks against critical infrastructure are of an even higher order of magnitude of concern for us, whether that's about a pipeline, or a meat supply, or a hospital system, or other areas of critical infrastructure. The president will talk to President Putin about our concerns on this front.”
In the run-up to the summit, Putin expressed openness to some kind of mutual exchange of cyber-criminals with the U.S. Biden said this was “potentially a good sign” but, in a follow-up, Sullivan pointed out that if people in the U.S. break the law, our system already holds them accountable, as opposed to how Moscow handles their citizens’ illicit activities. If Putin wants to start doing the same, then that’s great, but, Sullivan added: "This is not about exchanges or swaps, or anything like that."
Just after the summit concluded, the Washington Post noted that the expectations for “making any progress” at all on cyber were “set exceedingly low.” In their assessment, Biden cleared the bar. Other commentators agreed, with the USA Today Editorial Board noting “America reclaimed some lost pride Wednesday when President Joe Biden met in Geneva with Russian President Vladimir Putin—and did so without bowing and scraping to a smug and devious autocrat.” As for the assessment of Trump and his party apparatchiks, it was as hypocritical as anything they’ve said since 2016, and that really is saying something. The president himself expressed optimism going forward, and pushed back at those critics who might confuse his approach for naivete or a lack of guile. Always publicly focusing on the negatives, he argued, would simply “guarantee nothing happens.”
On the cyber-related specifics, first of all, Biden delivered to Putin the warning he’d promised:
Biden says Putin knows US has significant cyber capabilities...He “doesn’t know exactly” what they are, “but he knows they’re significant.”
— Richard Engel (@RichardEngel) June 16, 2021
Second, the two leaders came to an understanding on boundaries. Biden laid out the terms: “We agreed to task experts in both our countries to work on specific understandings about what's off-limits [for hacking] and to follow up on specific cases that originate in … either of our countries.” Putin, for his part, denied his government was behind any of the recent cyberattacks. While Trump may have accepted such a denial as truthful, Biden is, fortunately for us, not Trump.
Biden says he gave Putin a list of 16 areas of critical infrastructure that "should be off-limits" for cyberattacks, including the energy sector and water supply He says they agreed to have experts in their countries "work on specific understandings about what's off-limits" pic.twitter.com/K8oKdAFZ2J
— CBS News (@CBSNews) June 16, 2021
Here’s the takeaway in the words of James Lewis, who served in a high-level government position on cyber, “Biden delivered the right message. If the Russians didn’t know we were serious, it’s unavoidable now. But Putin isn’t going to make any concessions. They’re going to test us. …The next phase is coming up with ways to more comprehensively threaten them or to actually use our cyber capabilities.”
Regarding that next phase, on the heels of a NATO summit the weekend before last, the 30-nation alliance collectively declared: “the impact of significant malicious cumulative cyber activities might, in certain circumstances, be considered as amounting to an armed attack.” If such a determination was made, it could result in Article 5 being invoked. If that happened, all NATO member states would be required to come to the aid of the country facing attacks.
The NATO statement specifically cited Russia for having engaged in “malicious cyber activities; and turning a blind eye to cyber criminals operating from its territory, including those who target and disrupt critical infrastructure in NATO countries,” and continued: “we will make greater use of NATO as a platform for political consultation among Allies, sharing concerns about malicious cyber activities, and exchanging national approaches and responses, as well as considering possible collective responses. If necessary, we will impose costs on those who harm us.” This represents Joe Biden sending a message that cyberattacks on the U.S. will bring a response not just from us, but from our allies as well.
In summary, there’s a strong consensus that the 46th president is acting far more assertively as well as effectively on cyberattacks than did the 45th—especially in regards to Russia. Trump’s homeland security adviser Tom Bossert complimented Biden for having “indicated his willingness to hold Russia accountable in some way for the pipeline attack, even though it was carried out by a criminal organization,” and noted: “that's a big leap forward.” April Falcon Doss, who worked for more than ten years at the NSA, also praised the new administration’s approach.
In a success achieved in just the last two weeks, the Biden Department of Justice snatched back a majority of the loot ransomed by the Russian hackers who hit Colonial. I’d love to have been a fly on the wall (in the borscht?) when Vlad heard that news. People in the know when it comes to cybersecurity offered kudos on this action. Here’s what John Hultquist, an executive at FireEye, a cybersecurity company, had to say: “It has become clear that we need to use several tools to stem the tide [of ransomware attacks]…. A stronger focus on disruption may disincentivize this behavior, which is growing in a vicious cycle.” In other words, sometimes the best defense is a good offense.
Although China has also been responsible for a number of cyberattacks on the United States, including since Biden took office, it is clear that Russia is the primary bad actor on this front. One thing we know is that the current president will never be Vladimir Putin’s puppet—Trump, on the other hand, continues to be exactly that.
Trump's cringeworthy message is front and center on the Kremlin's propaganda networks. Russian state TV hosts, lawmakers and experts are grinning from ear to ear, like Cheshire cats. pic.twitter.com/hjVKrrvxww
— Julia Davis (@JuliaDavisNews) June 11, 2021
Republicans have long loved to trumpet their supposed credentials on national security. However, Democrats are in fact the ones who’ve better protected Americans from our adversaries abroad. Before 9/11, George W. Bush ignored Bill Clinton’s warning that Osama bin Laden would be our country’s greatest national security threat, and then went on to ignore multiple, specific warnings about an “imminent” attack that would result in “dramatic consequences”—and we’re not just talking about the famous “Bin Laden Determined to Strike in U.S.” presidential daily brief he received five weeks beforehand. That blunder, compounded by the decision to invade not only Afghanistan but Iraq, made Dubya the worst foreign policy and national security president in our history. Barack Obama, on the other hand, took out bin Laden and succeeded in leaving our country in a far better position than he found it on those fronts (as well as many others).
The Man Who Lost An Election And Tried To Steal It may not have done something as devastatingly harmful to our interests—not to mention the horrors unleashed on those living (and dying) in the region. Nevertheless, on cyberdefense, his lack of attention and lack of action were unconscionable. Trump’s malpractice left us highly vulnerable to the attacks we’ve faced in recent months, both before and after he grudgingly left office. President Biden will be judged on how well he is able to clean up the mess he inherited. He has already taken substantive steps toward achieving that objective.
Biden understands that the first and most important job of any president of the United States is to protect America, and today that includes protecting our computer systems and cyberinfrastructure. My gut tells me that he won’t let us down.
Ian Reifowitz is the author of The Tribalization of Politics: How Rush Limbaugh's Race-Baiting Rhetoric on the Obama Presidency Paved the Way for Trump (Foreword by Markos Moulitsas)